The RioRey is monitored and controlled through the rView console. This is a Java application that is able to communicate with one or more RioRey appliances through an SSH tunnel.
Updating the RIOS software is very straightforward: just load the new system definition into the appliance, indicate that an update has to be carried out and one reboot later you are done. The whole process only takes a few minutes of your time. Should anything go wrong, you can revert to a previous version in exactly the same way. During the upgrade, the network card is put in the hardware bypass mode, thus ensuring that the protected servers remain available.
The software is updated on more than a regular basis. RioRey does not employ a fixed schedule for updates - however, when we started our review we were using version 5.0.2, and by the time we were finishing it we could welcome version 5.0.5. It did not have any marked effect on the test results which version we used, so we did not repeat any of them.
However, it should be noted that the 5.0.5 update comes with protection against Slowloris. We tested it, of course - it turned out that the RX1810 is able to handle even those slow DoS attacks that hardly generate any traffic.
Operation
When the software is started an overview of the 'sensor network' is shown. Here you can check the status of all the RioRey appliances. You have to look around a bit to find certain settings and information, but it is not a configuration labyrinth, so with only a few clicks you will have found your way. There are two levels: system level and interface level.
At system level you can check the general status of the machine, such as the status of the various components, and CPU and memory load. In addition, at this level you can manage accounts, configure alerts and check various log files. Moreover, it is possible to renew the licence and carry out updates at this level.
At interface level, the application provides an overview of the network load of the LAN or WAN interface in question. In the basic versions of the RioRey appliances only incoming traffic is filtered and the application gives a fairly detailed overview of incoming traffic broken down into protocols (IP, TCP, UDP, ICMP) and per protocol into the percentage of bad packets and bytes and the number of invalid, filtered and whitelisted packets and bytes.
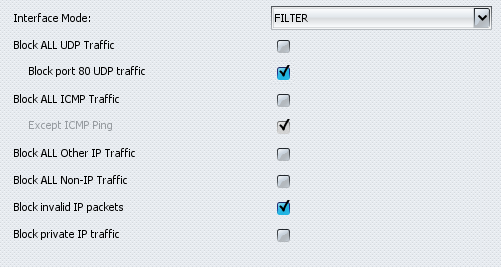
You can also configure the behaviour of the filters for every interface. Although we noted earlier that the RX1810 is not a firewall, it does contain a number of settings that relieve some of the workload of a firewall. For instance, there is a setting that allows you to block ICMP, UDP, non-IP and invalid packets and it is also possible to block traffic for local networks. In addition, the application offers three interface settings: 'filter' activates DDoS protection and 'monitor' analyses traffic but does not filter it. When set to 'bypass' the RioRey once again functions as an upgraded coupling device.
You can put a list of IP addresses on a whitelist or on a blacklist. Despite the fact that the application stores a mask with it, every IP address needs to be entered separately. This makes configuration somewhat toilsome when many IP addresses need to be entered into one (or both) of the lists.
The 'Service Definitions' deserve special mention as well. These allow you to indicate which traffic belongs to which IP addresses in the proprietary network. It is, for instance, possible to configure a web server in such a way that it only allows incoming TCP traffic to pass through ports 80 and 443. Other traffic is blocked, which, according to RioRey, has the effect of unburdening to a degree the (more complex) firewall at a spot further down the network.
Reporting
In addition to all these settings, rView offers an overview of the status of the various filters. Graphs show the amount of incoming traffic and the amount that is allowed to pass through. Per filter there are six 'confidence' levels that indicate to what extent traffic patterns resemble a DDoS attack. From level 3 upwards the appliance starts to filter incoming traffic.
The level is raised whenever successive analyses detect the same amount of (or more) suspicious traffic. In addition, the share of traffic involved in an attack is colour coded: traffic that is less than 5 percent suspicious gets a green colour, between 5 and 10 percent it gets a yellow colour, a percentage between 10 and 50 is coloured orange and if more than 50 percent of traffic is suspicious, the graph turns red.
/i/1268400082.png?f=thumb)
/i/1268400084.png?f=thumb)
If a filter reaches one of the two highest levels, the appliance in question in the 'network sensors' overview will turn orange or red, respectively. Moreover, an LED is switched on and warning e-mails and SNMP traps are sent.
To determine the load on the connection and how much of it is attack traffic, rView can produce various graphs. Subject to a slight delay, these graphs represent the latest traffic overview - both the aggregate amount of traffic and the amount after filtering are shown.
/i/1268400081.png?f=thumb)
/i/1268400083.png?f=thumb)
In addition, it is possible to request an overview of targets (or 'victims', as RioRey calls them, even though the appliance should of course stop the attacks before there are any victims) and attackers. The last overview in particular is somewhat redundant during a large DDoS attack because of the large number of entries. However, during regular use it is a useful overview to establish whether legitimate traffic gets blocked by accident. Moreover, it can be gathered from this overview that from some attackers only a few packets are stopped, while their IP address does not get blocked. It is also possible to enter IP addresses from this list into whitelists and blacklists.
